LoRa is one of the LPWAN communication technologies. It is an ultra-long-range wireless transmission scheme based on spread spectrum technology adopted and promoted by Semtech. This solution changes the previous trade-offs between transmission distance and power consumption, providing users with a simple system that can realize long-distance, long battery life and large capacity, and thus expand the sensor network. Currently, LoRa operates primarily in free global bands, including 433, 868, and 915 MHz.
Before diving into LoRa, let's start with the latest white paper from the LoRa Alliance and talk about LoRa.

The latest white paper from the LoRa Alliance: Complete end-to-end encryption for IoT application vendors
Security is a basic premise for all application scenarios, so security was designed from the beginning in the LoRaWAN protocol. However, security involves many aspects, especially the encryption mechanism of LoRaWAN requires special explanation.
So this white paper will explain the security of the current LoRaWAN protocol. First, the security attributes in the protocol will be explained, and then the specific implementation details will be presented. Finally, some LoRaWAN security designs will be explained.
LoRaWAN security properties
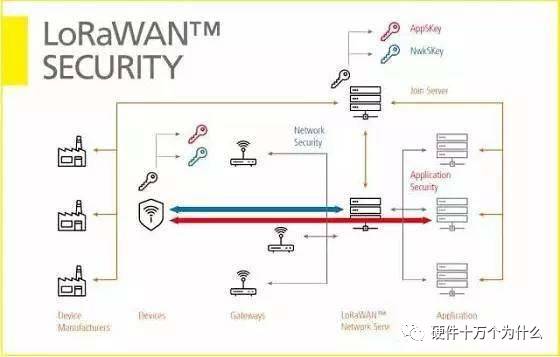
The security design principles of LoRaWAN are in line with the original intention of LoRaWAN, namely low power consumption, low complexity, low cost and large scalability. Because equipment is deployed on site and lasts for a long time (often several years), security considerations must be comprehensive and forward-looking. LoRaWAN security design follows advanced principles: adoption of standards, review of algorithms, and end-to-end security mechanisms. Next we describe the basic features of LoRaWAN security: including two-way authentication, integrity checking, and privacy mechanisms.
The process of two-way authentication as a network connection occurs between the LoRaWAN terminal node and the network. This ensures that only real and authorized devices can be connected to the real network.
LoRaWAN's MAC and application messages are "born" certified, integrity protected and encrypted. This protection, along with two-way authentication, ensures that network traffic is not changed, from a legitimate device, not to an "eavesdropper" or "rogue" device.
LoRaWAN security further provides an end-to-end encryption mechanism for data exchange between the terminal device and the server. LoRaWAN is one of the few IoT networking technologies that support end-to-end encryption. In traditional cellular networks, encryption occurs at the air interface, but in the carrier's core network it is simply transmitted as plain text.
Therefore, end users also need to select, deploy, and manage an additional layer of security (usually implemented by some type of VPN or application layer encryption such as TLS). However, this method is not suitable for use in LPWAN technology because it adds additional network power, complexity and cost. security strategy
The previously mentioned security mechanisms rely on well-tested and standardized AES encryption algorithms. The encryption community has been researching and analyzing these algorithms for many years and has been identified by the National Institute of Standards and Technology as the best security algorithm for nodes and networks.
LoRaWAN uses AES encryption statements combined with multiple modes of operation: CMAC for integrity protection, CTR for encryption. Each LoRaWAN terminal has a uniquely identified 128-bit AES Key (called AppKey) and another unique identifier (EUI-64-based DevEUI), both of which are applied to the device identification process.
The assignment of the EUI-64 identifier requires the applicant to obtain an Organizationally Unique Identifier (OUI) from the IEEE registration authority. Similarly, the LoRaWAN network is calibrated by a 24-bit globally unique identifier assigned by the LoRa Alliance.
Load for secure applications: LoRaWAN? End-to-end encryption of application workloads occurs between the terminal device and the server. Integrity protection is achieved by frequency hopping: Air frequency hopping provides integrity protection through LoRaWAN, and frequency hopping between the network and the server is achieved by using secure transmission schemes such as HTTPS and VPNS.
Two-way authentication: Air activation proves that both the terminal device and the network have the concept of AppKey. This is demonstrated by loading an AES-CMAC (using the AppKey) into the device's join request and backend receiver.
The two session keys are then mutually authenticated, one to provide integrity protection and encryption for the LoRaWAN MAC command and application load (NwkSKey), and the other to provide encryption for the end-to-end application load (AppSKey).
NwkSKey is loaded on the LoRaWAN network to verify the authenticity and integrity of the packet. From the perspective of the network operator, AppKey and AppSKey can be hidden, so it is impossible to crack the application load.
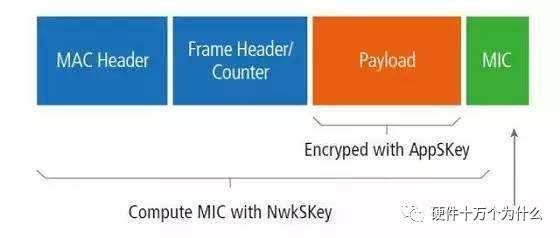
Data integrity and privacy protection: LoRaWAN communication is protected with two session keys. Each payload is encrypted by AES-CTR and carries a frame counter (to avoid packet playback), a message integrity code (MIC) and AES-CMAC (to avoid packet tampering). The figure below shows the structure of the LoRaWAN package.
Security facts and paradoxes: Physical security of LoRaWAN devices: AppKeys and derived session keys are continuously stored in LoRaWAN devices, and their security depends on the physical security of the device. Once the device is physically compromised, these keys are protected in tamper-resistant memory and are difficult to extract.
Cryptography: Some information indicates that LoRaWAN? passwords use only XOR and not AES. In fact, as mentioned earlier, AES is used in the standardized CTR mode, which takes advantage of XOR encryption operations (and many other modes such as CBC). This reinforces the AES algorithm by assigning a unique AES code to each block cipher.
Session Key Distribution: Since AppSKey and NwkSKey are generated from the same AppKey, it can be said that if the LoRaWAN operator obtains the AppKey, it can derive the AppSKey to decode the network.
Therefore, in order to avoid this situation, the server manages the storage of the AppKey, and the process of mutual authentication and key derivation can be operated by an entity other than the operator. In order to give operators additional flexibility, LoRaWAN's next new version of the protocol (1.1) will define two master keys, one for the network (NwkKey) and one for the application (AppKey).
Backend interface security: The backend interface includes control and data signals between the network and the application server. HTTPS and VPN technologies are used to secure the communication between these critical infrastructure elements.
Implementation and deployment security: The LoRa Alliance has been ensuring the security of its protocols and architecture specifications, but the overall security of the solution depends on the specific implementation and deployment. Therefore, security issues require cooperation in all aspects, and manufacturers, suppliers, and operators all need to participate.
Note 1 AES – an advanced encryption standard. This is a symmetric key based encryption algorithm that allows for message encryption and identity authentication.
2 CMAC – Code-based message authentication code.
3 CTR – Counter Mode Encryption Standard. A counter-based data stream encrypts the mode of operation of the AES algorithm.
4 AES-CMAC – Code-based message authentication code that uses AES encryption algorithms to provide message integrity and authenticity.
5 CBC is an operation mode of the AES algorithm, which relies on an initialization vector and a pre-ordered data block for data stream encryption.

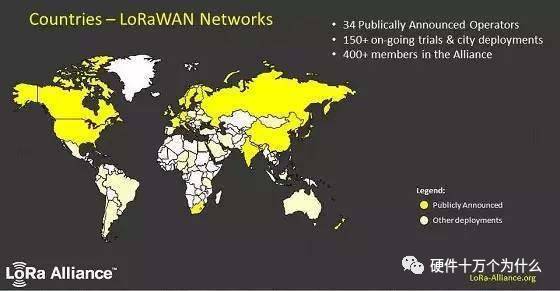
The final picture is a global deployment map from the LoRa Alliance. The LoRa Alliance currently has more than 400 members, more than 150 ongoing deployment plans worldwide, and 34 operators.
31 Q&A lists on Lora Q&A
1.) What is LoRa modulation? LoRa (Long Range) is a modulation technique that provides longer communication distances than comparable technologies. Modulation is based on spread spectrum technology, a variant of Linear Modulation Spread Spectrum (CSS) with Forward Error Correction (FEC).
LoRa significantly improves the acceptance sensitivity, and like other spread spectrum techniques, broadcasts a signal using the entire channel bandwidth, making channel noise and insensitivity due to the use of low-cost crystals more frequency offset.
LoRa can modulate the signal 19.5dB below the bottom noise, while most frequency shift keying (FSK) requires an 8-10dB signal power on the bottom noise to properly modulate. LoRa modulation is the physical layer (PHY) that can be used for different protocols and different network architectures - Mesh, Star, peer-to-peer, and more.
2.) What is LoRaWAN? LoRa modulation is a PHY, LoRaWAN is a MAC protocol for large-capacity long-distance low-power star networks, and the LoRa Alliance is standardizing on low-power wide area networks (LPWANs).
The LoRaWAN protocol is optimized for low-power, battery-powered sensors, including different levels of end nodes to optimize the balance between network latency and battery life. It is completely two-way and built by security experts to ensure reliability and security.
The LoRaWAN architecture also makes it easy to target mobile targets for asset tracking, the fastest growing application for the Internet of Things. Major telecom operators are deploying LoRaWAN as a national network, and the LoRa Alliance is standardizing LoRaWAN to ensure that different national networks are interoperable.
3.) What is a LoRa Gateway? The LoRa Gateway is designed for long-haul star architecture and is used in the LoRaWAN system. They are multi-channel, multi-modulation transceiving, multi-channel simultaneous demodulation, and even multi-signal demodulation on the same channel due to the characteristics of LoRa. The gateway uses a different RF device than the terminal node, has a higher capacity, and relays messages between the terminal device and the central network server as a transparent bridge.
The gateway connects to the network server through a standard IP connection, and the terminal device uses one-hop wireless communication to one or more gateways. The communication of all terminal nodes is generally two-way, but also supports such as multicast function operation, software upgrade, wireless transmission or other large-scale release of messages, thus reducing the wireless communication time. There are different gateway versions depending on the required capacity and installation location (home or tower).
4) What is the data rate of LoRaWAN? For LoRa, the LoRaWAN data rate ranges from 0.3 kbps to 11 kbps, and the European GFSK data rate is 50 kbps. In North America, the minimum data rate due to FCC is 0.9 kbps. To maximize the battery life and overall network capacity of the terminal device, the LoRaWAN network server manages each terminal device data rate and RF output separately through an adaptive data rate (ADR) algorithm.
ADR is critical to high-performance networks and is scalable. In terms of infrastructure, deploying a network with minimal investment, deploying more gateways when capacity is needed, ADR will enable higher data rates and expand network capacity by a factor of six to eight.
5.) What is the difference between LoRa technology and SIGFOX, NWave? In general, LoRa technology uses a spread spectrum technology; SIGFOX uses narrowband BPSK modulation technology; NWave uses the Weightless standard, which is similar to the technology used by SIGFOX. For detailed parameters, see "LPWAN Technology Comparison" in the menu dry goods data bar.
Companies that currently use ultra-narrowband technology have more transceiver chips to choose from, while LoRa can only use chips from Semtech.
6. What is the LoRa concentrator? Both the gateway and concentrator terms are used, but they are equivalent components in the LoRa system. In other industries, the definition of gateways and concentrators means different components.
7. How is LoRa processing interference? The LoRa modem can suppress the co-channel GMSK interference by up to 19.5 dB, or in other words, it can accept 19.5 dB of the signal below the interference signal or the bottom noise. Because of its strong anti-interference, the LoRaTM modulation system can be used not only in the frequency band with high spectrum usage, but also in the hybrid communication network to expand the coverage when the original modulation scheme fails in the network.
8. What is the rate of LoRa data? LoRaWAN defines a specific set of data rates, but a terminal chip or PHY can have multiple options. The SX1272 supports data rates from 0.3 to 37.5 kbps, and the SX1276 supports 0.018 to 37.5 kbps.
9. What is a LoRa endpoint or point? The LoRa endpoint is part of the LoRa network that is sensed or controlled. They are powered by a remote battery. These endpoints establish communication with the LoRa gateway (concentrator or base station) using the LoRaWAN network protocol.
10. What is Adaptive Data Rate (ADR)? ADR is a way to change the actual data rate to ensure reliable packet delivery, optimal network performance, and capacity scale. For example, nodes close to the gateway use higher data rates (shortening transmission time) and lower output power. Only the nodes that are very marginal on the link budget use the lowest data rate and maximum output power.
The ADR approach can accommodate changes in network infrastructure and support changing path losses. To maximize the battery life and overall network capacity of the terminal equipment, the LoRa network infrastructure manages the data rate and RF output of each terminal device separately by implementing ADR.
11. What is the actual Tx power that can be achieved on the LoRa device antenna? The power output at the pin of the chip is +20dBm. After the matching/filtering loss, the power on the antenna is +19dBm +/-0.5dB. The maximum output power has different regulations in different regions. The LoRaWAN specification defines different output powers in different regions to maximize the link budget.
12. What is the price of the LoRa solution? LoRa devices such as the SX1272 or SX1276 use a lower cost crystal. In narrowband technology, an expensive temperature-controlled crystal oscillator is required during RX/TX transceiving to reduce frequency drift. Depending on volume and functionality, a typical bill of materials cost for a complete endpoint is $2 to $5.
Long transmission distances mean that the network infrastructure is simplified because there is no need for relay deployment costs. Lower power consumption means lower cost battery and network maintenance. 13. What is the process of LoRa Channel Activity Detection (CAD) mode? CAD is used to detect the presence of a LoRa signal, rather than using a Received Signal Strength (RSSI) method to identify if a signal is present. It distinguishes between noise and the LoRa signal that is needed. The CAD process requires two symbols. If detected by CAD, the CAD_Detected interrupt becomes active and the device is in RX mode to accept the data payload. 14. Why does my LoRa device or module output less than 20dBm? The +20dBm specification is for the chip pin output power. In any RF system, the bandpass filter and the RF switch have insertion loss characteristics, and the typical performance of the matched filter can reach +19 dBm.
15. Can I change the mode frequently between FSK and LoRa modulation?
Yes, no problem. The LoRa device can be switched from FSK to LoRa (and vice versa) with a simple SPI register write. There is no impact on the performance and reliability of the device. The LoRa device can be configured or reconfigured to any parameter as specified in the data sheet.
16. If you can't reach +20dBm, how to solve the output power problem?
1.) Make sure that you are connected to the correct pin (PA_Boost) setting, 20dBm output pin. There are two output ports per band. One is a high-power port called PA_boost, and the other is a high-efficiency port called RFO.
2.) Then, check the software configuration. Three registers should be properly configured: RegPaConfig, RegOcp, and RegPaDac. This means that you should select the correct pin in the software to make the appropriate output, and then set the correct value according to the power level you need.
3.) Verify that they are consistent with the Semtech reference design in order to design a good PCB layout. This is important for the maximum possible output power.
17. How does the LoRa system achieve mass production testing?
There are three important parameters to be tested in mass production: frequency tolerance, output power, and sensitivity. The frequency and output power are easily tested using a spectrum analyzer. If your signal generator cannot generate a LoRa signal, it is highly recommended to use the FSK mode to test sensitivity. There is only one RF link in the chip, and both FSK and LoRa are modulated in the digital domain.
The RF path may be assembled incorrectly (such as a virtual solder), so verification is important. The digital portion of the chip LoRa and FSK modulation is not affected by the assembly, so it is sufficient to verify the FSK sensitivity for verifying the production test performance.
18. How do I choose the right crystal for my LoRa device?
Normally, for most designs, a bandwidth of 62.5 kHz or higher, a +/- 10 ppm XTAL is sufficient. The bandwidth is less than 62.5 kHz and TCXO is highly recommended.
For more details on crystal specifications, please refer to the data sheet and LoRa Modem Calculator Tool and Application Note – AN1200.14_XO_Gidance_LoRa_Modulation_STDâ€.
19. How do you measure frequency accuracy in LoRa mode for LoRa bandwidth signals?
If only for measurement, you can use the frequency synthesizer TX (FSTX) mode, as listed in the LoRa register table, to generate a CW tone based on the LoRa configuration.
20. What is the relationship between signal bandwidth (BW), symbol rate (Rs), and data rate (DR)?
In theory, Rs=BW/(2^SF), DR= SF*(BW/2^SF)*CR, but we recommend that you use the Semtech LoRa modem calculator to evaluate the data rate and transmission time according to different configuration options. 21. How to choose LoRa signal bandwidth (BW), spreading factor (SF) and coding rate (CR)?
LoRaWAN primarily uses a 125 kHz signal bandwidth setting, but other proprietary protocols can utilize other signal bandwidth (BW) settings.
Changing BW, SF, and CR also changes the link budget and transmission time, and requires a trade-off between battery life and distance. Please use the LoRa modem calculator to evaluate the trade-offs.
22. What are the steps for fault detection when the SX127x modules from two different manufacturers cannot communicate with each other?
First, check the frequency offset caused by the crystal between the two devices. Bandwidth (BW), center frequency, and data rate are all derived from the crystal frequency. Second, check the software/firmware settings on both sides to ensure that the frequency, bandwidth, spreading factor, coding rate, and packet structure are consistent.
23. In LoRa mode, how can I receive an erroneous packet when the Cyclic Redundancy Check (CRC) is enabled?
In LoRa mode, the payload is added to the FIFO even if the CRC is wrong. The PayloadCrcError must be checked for its integrity before the payload is taken. In the Explicit Header mode, there is a small possibility that a false detection produces a "clone" packet.
Either the wrong header opens the CrcOn bit, then the payload will be wrong, the modem will mark it as a PayloadCrcError condition, so the packet is easily filtered out; or the wrong header disables the CrcOn bit, in which case the pattern considers The packet is good. These occasional bad packets will have a random length (extracted from the error header information) and are easily filtered out by the host, for example to see the size of the exception.
24. Can I send or accept an unlimited length payload packet with a LoRa device?
No, the maximum packet length in LoRa mode is 256 bytes.
25. How do I use the DIOx pin in LoRa mode? Are all DIOx pins connected to the MCU?
When you start designing, check the DIO mapping in both LoRa and FSK modes. You can find DIO mapping information in the SX127x LoRa data sheet. DIO does not have the same functionality as the usual (typical) MCU GPIO. There are some special interrupt messages (or clock outputs) that indicate event or chip status, which makes your firmware design easier to implement.
In theory, you may not be connected to the DIO pin, then poll the relevant registers to know the status result. Of course, we recommend connecting DIO as much as possible as an external interrupt function, saving the MCU's resource load and allowing for a very low-power mode of operation (the MCU sleeps when packaged to send or receive packets).
26. Why are there two RSSI registers in LoRa mode? What's the difference?
Both RegPktRssiValue and RegRssiValue registers are useful in LoRa mode. RegPktRssiValue refers to the packet RSSI level, and RegRssiValue is similar to the RSSI in FSK mode (non-LoRa mode).
As you know, LoRa can demodulate packets below the noise floor (PktRssi result), then CurrentRssi is equal to or greater than the bottom noise. For more information on how to calculate the values ​​of these two RSSIs, please refer to the Semtech API or the latest LoRa data sheet.
27. How do I calculate the actual bit rate and transmission time of the LoRa system?
The steps (iV) are listed below: It is easy to calculate by using the LoRa calculator, which can be downloaded from the Semtech website (link below). Http://?file=SX1272LoRaCalculatorSetup1%271.zip
28. The payload length of LoRa mode can be configured to 256 bytes at any data rate.
The SX127x LoRa device has a 256-byte FIFO in LoRa mode. In theory, all 256 bytes can be used for TX or RX. However, with a low data rate configuration, the transmission time of a 256-byte payload will be very long (several seconds or longer), which is not good for anti-fading and high-interference environments.
This is not a robust configuration in most environments, so it is recommended that if you want to use a payload with a low data rate, the packet can be broken into several short packets.
29. Is LoRa a mesh network, peer-to-peer, or a network?
LoRa itself is a PHY that can be used for all network topologies. Mesh networks extend the reach of the network, but at the expense of reduced network capacity, synchronization overhead, and battery life, due to synchronization and hop count. The LoRa gateway and the module are networked in a star network mode, and the LoRa modules can theoretically be networked in a point-to-point polling manner. Of course, the point-to-point polling efficiency is much lower than that of the star network.
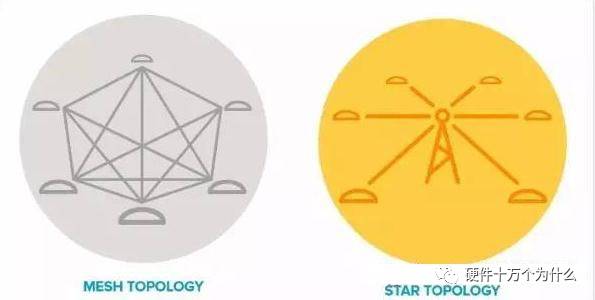
As LoRa's link budget and distance range increase, there is no need to extend the distance with the mesh network architecture, so LoRaWAN chooses a star architecture to optimize network capacity, battery life, and ease of installation.
30. Can LoRa use IPv6 and 6LoWPAN?
Yes, LoRa is compatible with IPv6 and 6LoWPAN. Actility (LoRa Partner) and other partners implemented 6LoWPAN on LoRaWAN.
31. What is the capacity of the LoRa Gateway? How many nodes can a gateway connect to?
First and foremost, capacity is a result of the number of packets accepted in a given period of time. An SX1301 has eight channels and can accept nearly 1.5 million packets of data per day using the LoRaWAN protocol. Therefore, if your application sends a packet every hour, an SX1301 gateway can handle approximately 62,500 end devices.
It is understood that the LoRa Alliance and the NB-IoT Alliance are rushing to grab the Internet of Things market. Due to the different technical characteristics and applicable scenarios, it is difficult to meet customer needs in one stop. At present, Xiecheng Smart has a successful case and rich industry solutions. It is also a member of CLAA (LoRa Alliance) and China NB-IoT Industry Alliance. It provides a one-stop LoRa solution (compatible with NB-IoT), including LoRa modules. NB-IoT module + IoT base station + management platform software open source + data supply, etc., can be customized for development, the market is preferred.
A new rule from the Drug Enforcement Administration (DEA) threatens to upend the American hemp industry, and could even result in criminal prosecutions for manufacturers of CBD and delta-8 THC products.
The DEA says the [interim final rule," issued Aug. 20, is simply a matter of adjusting its own regulations to account for changes to the Controlled Substances Act that were mandated by the 2018 Farm Bill (or Agricultural Improvement Act) that legalized hemp and CBD production. The new rule [merely conforms DEA`s regulations to the statutory amendments to the CSA that have already taken effect," says the agency. The new rule doesn`t break any ground, according to the DEA.
But many experts on cannabis and hemp law say the DEA rule creates a potential pathway the law enforcement agency could use to prosecute hemp processors and producers of CBD (cannabidiol) and delta-8 THC (or Δ8THC) products. There are two issues: partially processed CBD, and [synthetically derived" delta-8 THC.
Cbd Pod System Oem,Cbd Vape Pod Oem,Best Cbd Pod System,Cbd Pod System
Shenzhen MASON VAP Technology Co., Ltd. , https://www.disposablevapepenfactory.com
