Because of the need for interaction, Amazon Echo is always listening to people, so it is also easy to be paranoid as a listener. Recently, an experiment by a security researcher told us that there is no clear security line between the cute speaker and the evil listener. With just a few minutes of operation, hackers can convert Echo into a tapping microphone without leaving any traces. A report by wired introduced the experiment, and finally gave everyone the final solution.
British security researcher Mark Barnes detailed the technology for installing malware in Amazon Echo in a lab blog. Practice has proven that his code can secretly pass audio to his own server. This technique first needs to be done first and foremost on Echo's physical objects, and only works for Echo sold before 2017. Barnes warned that for those products sold before 2017, the vulnerability could not be fixed by software, and the modified Echo did not have any flaws in appearance.

Although the emergence of this technology does not make every Echo user fearful, it does point out the security problems in Echo. As sales increase, people will carry Echo out. More and more Echo is left in hotel rooms or offices, and users can't keep an eye on it, leaving opportunities for people who don't care.
Transform Echo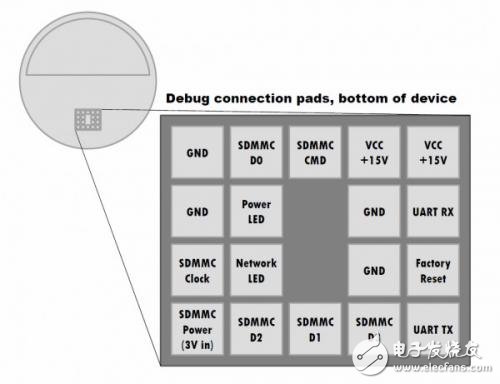
“We showed a root Echo technology and turned it into a 'snuggle',†said Barnes, a security researcher at the MWR lab in Basingstoke, England. His blog describes how he installed his own malware on Echo, first creating a "root shell" that allows him to connect to the hacked Echo over the Internet, and finally "remotely monitor" Ehco for continuous recording.
This method takes advantage of Echo's legacy hardware security vulnerabilities sold before 2017. Removing Echo's rubber base reveals some of the metal pads underneath, which are linked to internal hardware and should be used to test and fix errors before they are sold. For example, one of the metal disks can read data from the SD card.
Echo's metal pad distribution
Barnes then connected two small metal disks by soldering, one connected to his laptop and the other connected to an SD card reader. Then, he used Amazon's own features to load his modified Echo "boot loader" from the SD card. This program is rooted in some hardware devices, can wake up the operating system itself, can also adjust the operating system's authentication measures, and allows him to install software on Echo.
Although soldering takes hours and leaves physical evidence, the wires that connect the extensions are distributed everywhere, but Barnes said that as the development progresses, plugging in special devices allows them to connect directly to these. Pads, easily achieve the same effect in minutes. In fact, an early paper by a research team at the Castle Military Academy in South Carolina also supported Barnes's argument that the hacker could connect to the pad using a 3D printed device.
Barnes explained: "As long as this small rubber bottom, you can connect these pads directly. You can make a device that can be plugged in so that there is no need to solder, and there will be no obvious traces of operation."
After the software he wrote got the ability to connect to Echo, Barnes wrote a simple script that could control the microphone and transfer the audio to any designated remote computer. He pointed out that such software can easily perform other evil functions, such as using it as an access point to attack other parts of the network, stealing a user's Amazon account, or installing other ransomware. Barnes said: "You can use it to do whatever you want, really."
Simple trickAmazon has fixed the security vulnerability of Echo discovered by Barnes in the latest version. Barnes said that Amazon has put an end to this possibility in hardware products. When WIRED asked Amazon about the matter, Amazon wrote in a statement: "To ensure product safety, we recommend that customers purchase Amazon-made devices from Amazon or trusted retailers and keep software updates. â€
Barnes agrees that his experiment is mainly a warning to those who buy Echo from a channel other than Amazon. For example, some used Echo may have been modified. But he also pointed out that the software update is not able to save the early Echo, because the problem lies in the hardware loopholes.
He said people should consider using Echo's security risks in public or semi-public settings, such as the Wynn Las Vegas, and plan to place Echo in every room. Barnes said: "In this case, you simply can't know who is connected to Echo. "Maybe the hotel's previous guests installed something inside, or a cleaner, who is suspect. "The idea of ​​turning indoor smart service devices into spyware is not just a paranoid: WikiLeaks released a document indicating that the CIA has developed a similar physical access technology to turn Samsung smart TV into a wiretap device. .
For those who are worried that Echo has been transformed, Barnes pointed out that Amazon still has a hand, Echo has a mute button, which is also Echo's switch, which cannot be bypassed by malware. He recommended this method: "If the button is closed, there is no way to restart the software," he said.
So this is his trick: "One is the spirit."
Two - way trigger diode, also known as two - end ac device (DIAC), and two - way thyristor at the same time.Because of its simple structure and low price, it is often used to trigger the bidirectional thyristor, and can also constitute overvoltage protection circuits.Construction, symbol and equivalent circuit of a bidirectional trigger diode.
Also commonly used in the overvoltage protection, timing, shift equal circuit, Figure 2 is the overvoltage protection circuit composed of bidirectional trigger diode and bidirectional thyristor.When the transient voltage exceeds the DIAC and Ubo, the DIAC quickly conducts and triggers the bidirectional thyristor to also conduct, so that the following load is protected from overvoltage damage.

DO-35,DIACS,DO-35 Diode,DO-35 package,Small Signal Diode
Changzhou Changyuan Electronic Co., Ltd. , https://www.cydiode.com
