As we all know, Secure Shell, also known as SSH, is an encrypted network protocol that allows you to securely access/communicate between an unsecured network (such as the Internet) and a remote system. Whenever SSH is used to send data over an unsecured network, it will be automatically encrypted on the source system and decrypted on the destination system. SSH provides four encryption methods, password-based authentication, key-based authentication, host-based authentication and keyboard authentication. The most commonly used authentication methods are password-based authentication and key-based authentication.
In password-based authentication, all you need is the password of the user on the remote system. If you know the password of the remote user, you can use ssh user@remote-system-name to access the respective system. On the other hand, in key-based authentication, in order to communicate through SSH, you need to generate an SSH key pair and upload the SSH public key to the remote system. Each SSH key pair is composed of a private key and a public key. The private key should be stored on the client system, and the public key should be uploaded to the remote system. You should not disclose your private key to anyone. Hope you have a basic concept of SSH and its authentication methods.
In this tutorial, we will discuss how to configure SSH with key-based authentication on Linux.
Configure SSH with key-based authentication on Linux
To facilitate the demonstration, I will use Arch Linux as the local system and Ubuntu 18.04 LTS as the remote system.
Local system details:
OS: Arch Linux Desktop
IP address: 192.168.225.37/24
Remote system details:
OS: Ubuntu 18.04 LTS Server
IP address: 192.168.225.22/24
Local system configuration
As I said before, in the key-based authentication method, if you want to access the remote system through SSH, you need to upload the public key to the remote system. The public key is usually stored in a file ~/.ssh/authorized_keys on the remote system.
Note: Do not use the root user to generate the key pair, so that only the root user can use it. Use ordinary users to create key pairs.
Now, let's create an SSH key pair on the local system. Just run the following command on the client system.
$ ssh-keygen
The above command will create a 2048-bit RSA key pair. You need to enter the password twice. More importantly, remember your password. It will be used later.
Sample output:
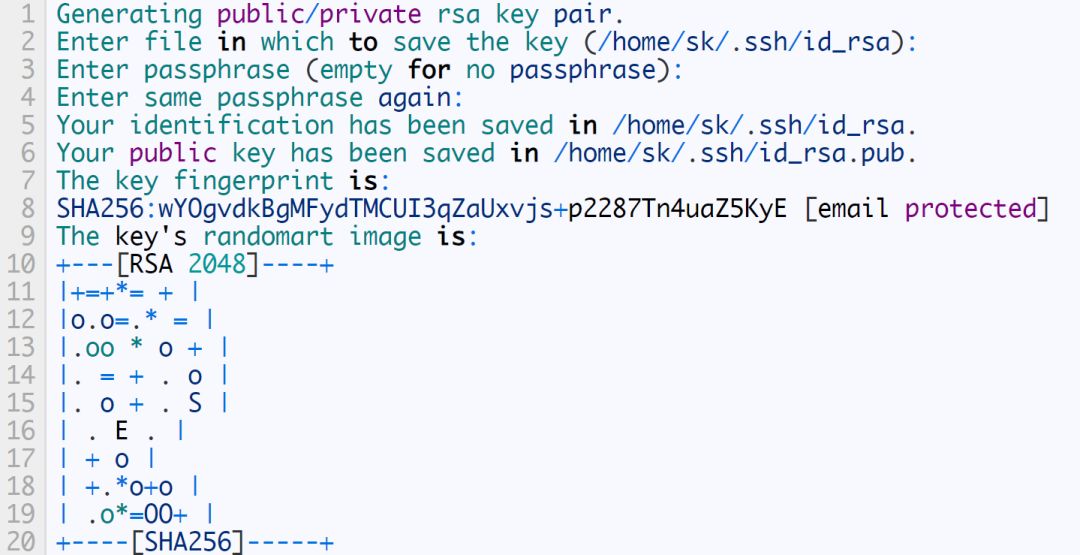
If you have created a key pair, you will see the following message. Typing y will overwrite the existing key.
/home/username/.ssh/id_rsa alreadyexists.
Overwrite(y/n)?
Please note that the password is optional. If you enter a password, you will be asked to enter the password every time you access the remote system through SSH, unless you use an SSH agent to save the password. If you don't want a password (although it is not secure), simply hit enter twice. However, I suggest you use a password. From a security perspective, using a passwordless ssh key pair is not a good idea. This method should be limited to use in special circumstances, for example, service access to remote systems without user intervention. (For example, remote backup with rsync...)
If you already have a password-less key in your personal file ~/.ssh/id_rsa, but want to update to a key with password. Use the following command:
$ ssh-keygen -p -f ~/.ssh/id_rsa
Sample output:
Enternewpassphrase(emptyfornopassphrase):
Enter same passphraseagain:
Your identification has been saved with thenewpassphrase.
Now, we have created the key pair on the local system. Next, use the following command to copy the SSH public key to your remote SSH server.
$ ssh-copy-id .22
Here, I copied the public key on the local (Arch Linux) system to the remote system (Ubuntu 18.04 LTS). Technically speaking, the above command will copy the contents of the local system ~/.ssh/id_rsa.pub file to the remote system ~/.ssh/authorized_keys. do you understand? It's great.
Enter yes to continue connecting to your remote SSH server. Next, enter the password of the remote system user sk.
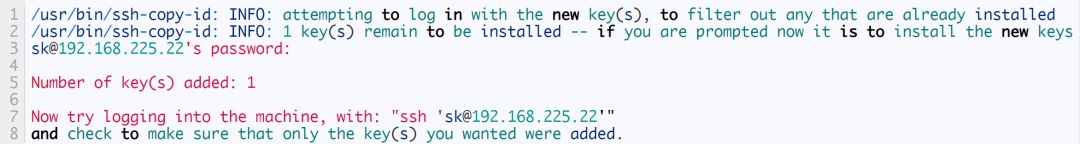
If you have copied the key but want to replace it with a new password, use the -f option to overwrite the existing key.
$ ssh-copy-id -f .22
We have now successfully added the SSH public key of the local system to the remote system. Now, let us completely disable password-based authentication on the remote system. Because we have configured key authentication, password authentication is no longer required.
Disable password-based authentication on SSH on the remote system
You need to execute the following commands as root user or sudo.
To disable password-based authentication, you need to edit the /etc/ssh/sshd_config configuration file in the terminal of the remote system:
$ sudo vi /etc/ssh/sshd_config
Find the following line, uncomment it and set the value to no:
PasswordAuthentication no
Restart the ssh service for it to take effect.
$ sudo systemctl restart sshd
Access remote system from local system
Use the command to SSH your remote server on the local system:
$ ssh .22
enter password.
Sample output:
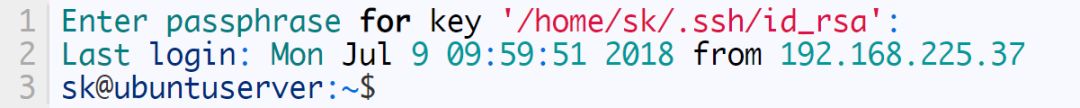
Now, you can SSH your remote system. As you can see, we have used the password created by ssh-keygen to log in to the account of the remote system, instead of using the actual password of the current account.
If you try to ssh from another client system (remote system), you will get this error message. For example, I tried to access the Ubuntu system from CentOS SSH through the command:
Sample output:
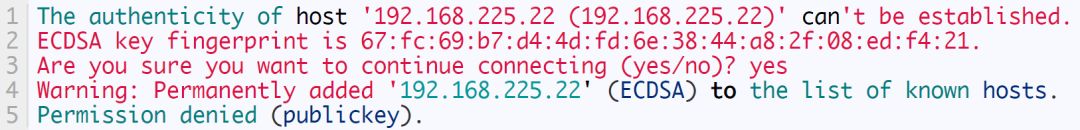
As you can see, apart from the CentOS (LCTT Annotation: According to the above, this should be Arch) system, I cannot access my remote system Ubuntu 18.04 through SSH from any other system.
Add more client system keys to the SSH server
This point is very important. Like I said, unless you configure it (in the previous example, Ubuntu), you cannot access the remote system via SSH. If I want to give more clients permission to access the remote SSH server, what should I do? It's very simple. You need to generate SSH key pairs on all client systems and manually copy the ssh public key to the remote server you want to access via ssh.
Create an SSH key pair on the client system and run:
$ ssh-keygen
Enter the password twice. Now, the ssh key pair has been generated. You need to manually copy the public key (not the private key) to the remote server.
Use the following command to view the public key:
$ cat ~/.ssh/id_rsa.pub
It should output a message similar to the following:
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCt3a9tIeK5rPx9p74 / KjEVXa6 / OODyRp0QLS / sLp8W6iTxFL + UgALZlupVNgFjvRR5luJ9dLHWwc + d4umavAWz708e6Na9ftEPQtC28rTFsHwmyLKvLkzcGkC5 + A0NdbiDZLaK3K3wgq1jzYYKT5k + IaNS6vtrx5LDObcPNPEBDt4vTixQ7GZHrDUUk5586IKeFfwMCWguHveTN7ykmo2EyL2rV7TmYq + eY2ZqqcsoK0fzXMK7iifGXVmuqTkAmZLGZK8a3bPb6VZd7KFum3Ezbu4BXZGp7FVhnOMgau2kYeOH / ItKPzpCAn + dg3NAAziCCxnII9b4nSSGz3mMY4Y7 ostechnix @ centosserver
Copy all the content (via a USB drive or any other medium), then go to the terminal of your remote server, as shown below, create a folder called .ssh under $HOME. You need to execute commands as root (note: root is not necessarily required).
$ mkdir -p ~/.ssh
Now, add the public key of the client system created in the previous steps to the file.
echo {Your_public_key_contents_here} >> ~/.ssh/authorized_keys
Restart the ssh service on the remote system. Now, you can SSH the remote server on the new client.
If you find it difficult to add the ssh public key manually, temporarily enable password authentication on the remote system, use the ssh-copy-id command to copy the key from the local system, and finally disable password authentication.
Ultra Thin Battery,Ultra Slim Battery Pack,Thin Lithium Ion Battery,Ultra Light Optics Battery,Polymer lithium battery,Cylindrical Lithium Battery
Langrui Energy (Shenzhen) Co.,Ltd , https://www.langruibattery.com
