Introduction With the continuous application of contactless logic encryption cards, the technical deficiencies are increasingly exposed, and it is difficult to meet the needs of higher security and more complex multi-applications. In 2008, the method of cracking the password of the Mifare Classic IC chip (M1 chip) was published on the Internet; German researcher Henryk Plotz and Dr. Karsten Noh1 of computer science at the University of Virginia. Successfully cracked the security algorithm of NXP's Mirare classic chip; two independent research groups from the University of Virginia and the University of Radboud in the Netherlands confirmed the vulnerability of the Mi-fare chip and published a paper on cracking the chip encryption algorithm. Demonstrates the cracking process of the actual operation chip.
After the cracking of the incident, the Dutch Minister of the Interior Minister Horst said in an interview with the media that one of the world's 1 billion IC cards can be easily cracked. After the cracking of the storm was reported by the domestic media, it caused a great uproar in China. The application of urban public utility IC card as a non-contact logical encryption card has forced us to calm down and seriously consider the urban public utility IC card system. Security issues and future directions. If you master the cracking technology, criminals can illegally recharge or copy all kinds of "one card" and access control cards that use the chip at a low economic cost, which will bring great social security risks. Therefore, the non-contact CPU smart card technology is becoming a technologically up-and-coming option, and the era of replacing logical encryption cards with CPU cards has arrived.
This article refers to the address: http://
1 Non-contact logic encryption card Mifare card security issues Philips (now NXP) Mifare 1 card, which accounts for 80% of the global market share in contactless card applications, is the current industry standard for contactless smart cards, and also becomes ISO14443- A working draft.
Mifare's security authentication relies on the independent KEYA and KEYB check of each sector. It can realize the read and write security control of sector data through the different security combinations of sector control words and KEYA and KEYB. Its personalization is also relatively simple, mainly including data and updates of each sector KEYA, KEYB, in which all sensitive data (including KEYA and KEYB) are directly updated in clear text.
The verification mechanism of KEYA and KEYB can only solve the card-to-terminal authentication, but cannot solve the terminal-to-card authentication, that is, there is a risk commonly known as "pseudo-card".
Mifare's key is a pre-set fixed password. No matter what method is used to calculate the key, it must be consistent with the previously written fixed password to read and write the protected data. Therefore, whether it is a one-card-one-density system or a unified password system, the decryption of the contactless logical encryption card can be realized after being cracked. There is a view that as long as the ID number of a card-one-density, real-time online system, or non-contact logical encryption card is used, the key can be prevented from being decrypted. In fact, the decryption of the contactless logical encryption card means that the M1 card can be copied. Although the online system can avoid being illegally recharged, but cannot guarantee illegal consumption, that is, copying an M1 card with the same ID number, it can be illegally consumed. . Today's technology can be completely replicated using an FPGA. Based on this principle, Mifare's access card is also unsafe.
2 Features and advantages of non-contact CPU card Non-contact CPU card, also known as smart card, integrated circuit in the card with microprocessor CPU, storage unit (including random memory RAM, program memory ROM (Flash), user data memory EEPROM ) and the chip operating system COS. The CPU card with COS is equivalent to a microcomputer, which not only has data storage function, but also has functions such as command processing and data security protection.
The contactless CPU smart card has the following characteristics compared with the contactless logical encryption card:
1 chip and COS security technology provides a double security guarantee for the CPU card;
2 has an independent CPU processor and chip operating system;
3 The requirements for the computer network system are lower, the offline operation can be realized, and the one-card multi-purpose in the true sense can be realized, and each application is independent from each other and controlled by the respective key management system;
4 The transaction automatically guarantees the integrity of the data (anti-extraction);
5 can more flexibly support a variety of different application needs, more secure design transaction process;
6 independent security module - use the corresponding physical SAM card key to achieve encryption, decryption and transaction processing, thus completing the security authentication with the user card.
The advantages of a contactless CPU smart card are:
1 advanced. The CPU card can be used as a bank's financial card, representing the highest level of security for current IC card applications, and is becoming a mainstream product in IC card applications.
2 normative. Support T0, T=1 communication protocol in accordance with ISO7816-3 standard, comply with China Financial Integrated Circuit (IC) Card Specification and China Financial Integrated Circuit (IC) Card Application Specification, and support e-wallet that conforms to bank regulations. , electronic passbook function.
3 compatibility. Due to the unified regulations and strict testing of the People's Bank of China, the CPU card has good compatibility and security. The chip and COS security technology provides a dual security guarantee for the CPU card; supports encryption algorithms such as DES and TripleDES, supports line encryption and line security functions, prevents communication data from being illegally stolen or tampered, and uses process keys to implement encryption and decryption.
4 scalability. The card supports a variety of capacity options, such as 2 KB, 4 KB, 8 KB, 16 KB, 32 KB of EEPROM space. The CPU card can be easily extended to a variety of applications from the card structure to the card capacity, and can be combined with the bank to achieve a true multi-card use.
5 security. Compared with the logical encryption card, since the smart card has a CPU chip inside, it has the ability of data judgment and data analysis processing capability. Therefore, the smart card can distinguish between legal and illegal read and write devices at any time, and because of the CPU chip, The data computing capability can also encrypt and decrypt data, so it has very high security. The CPU card is also packaged with a microprocessor chip (CPU) while the EEPROM chip is packaged on the card. In this way, the data interface of the EEPROM is not connected to the external data line of the IC card under any circumstances. The external read/write device can only exchange data with the EEP-ROM in the IC card, and in any case, it can no longer access any unit in the EEP-ROM.
When the external read/write device exchanges data with the smart card, it must first issue an instruction to the CPU, and the CPU interprets the instruction according to the card operating system (COS) stored in the internal ROM, and performs analysis and judgment. After confirming the legitimacy of the read/write device, the external read/write device is allowed to establish a connection with the smart card. After the data operation, the external read/write device still issues a corresponding instruction, and the CPU correctly interprets the instruction, allowing the external read/write device and The data storage area (RAM) in the smart card exchanges data. After the data exchange is successful, under the control of the CPU, the internal data bus in the smart card is used, and the data in the internal RAM is exchanged with the data in the EEPROM. This achieves a secure protection of the data in the smart card EEPROM and therefore has a very high security.
3 Features and performance of non-contact CPU card FM1208 FM1208 is a single-interface non-contact CPU card chip designed by Fudan Microelectronics Co., Ltd. ISO14443-A protocol, hardware DES coprocessor, built-in 8 KB EEPROM. The FM1208 features compatibility with the widely used contactless logic encryption cards, combining the functions of a contactless logical encryption card (Mirare algorithm) and a bank-compliant contact CPU card.
Features: Communication protocol is ISO14443-A; MCU instruction is compatible with 8051; supports 106 kbps data transmission rate; Triple-DES coprocessor; program memory 32K×8-bit ROM; data memory 8K×8-bit EEPROM; 256×8-bit iRAM; 384 × 8 bit xRAM; low voltage detection reset; high and low frequency detection reset; EEPROM meets 100,000 erase and write indicators and 10 years of data retention indicators.
Typical processing time of FM1208:
â—† Identify a card time of 3 ms (including reset response and anti-collision);
â—† EEPROM erase time is 2.4 ms;
â—† Typical transaction process <350 ms.
Security mechanism of FM1208:
â—†There is a reverse power analysis module;
â—† There is a high and low frequency detection reset module, the chip working frequency is automatically reset beyond the detection range;
â—† ROM anti-reverse extraction, memory data encryption.
The functional block diagram of FM1208 is shown in Figure 1.
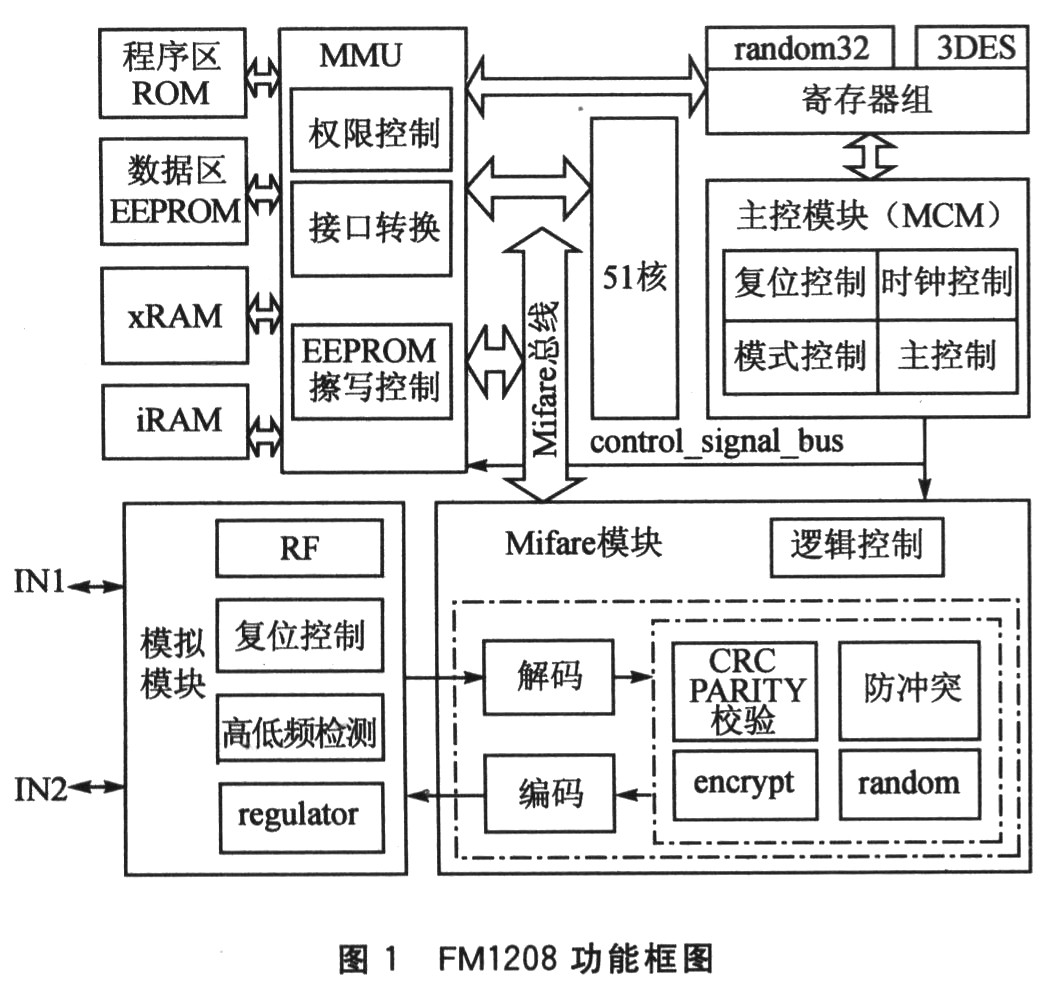
4 COS of the contactless CPU card FM1208
Due to the high security of the CPU card and the fact that one card supports multiple applications, the range of CPU cards used in the IC card family is expanding. Similar to a computer, the CPU card also has a CPU, memory and input and output interfaces, so the CPU card must also require an operating system in the application. Shanghai Fudan Microelectronics Co., Ltd. successfully developed the FMCOS (FMSH Card Operating System), a proprietary CPU card operating system. The operating system complies with the ISO7816 series of standards and the "China Financial Integrated Circuit (IC) Card Specification", which is applicable to many applications such as insurance, medical care, social security, public utility charges, security control, documents, transportation, etc., especially in finance. field.
FMCOS specifies three basic applications: e-wallet, electronic passbook and Easy Entry.
The characteristics of FMCOS are as follows:
1 Supports Single DES and Triple DES algorithms, and automatically selects the Single DES and Triple DES algorithms according to the length of the key.
2 Support line encryption and line protection functions to prevent communication data from being illegally stolen or tampered with.
3 supports multiple different applications on one card: a three-level directory can be created.
4 support the e-wallet function, the wallet size can be set by the user.
5 supports a variety of file types, including binary files, fixed-length record files, variable-length record files, loop files, wallet files.
6 supports ISO7816-3: T = 0 (character transfer) communication protocol.
7 Meet bank standards: in line with China Financial Integrated Circuit (IC) Card Specifications.
8 anti-plug function: the card that is not normally pulled out during transaction processing is automatically restored.
FMCOS consists of four functional modules: transmission management, file management, security system, and command interpretation.
1 Transmission management: According to the ISO7816-3 standard, the communication between the card and the terminal is supervised to ensure the correct transmission of data, and the communication data between the card and the terminal is prevented from being illegally stolen and falsified.
2 file management: store user data in EEP-ROM as a file to ensure the speed and data security when accessing files.
3 Security System: The security system is the core part of FMCOS. It involves the identification and verification of cards and the authority control mechanism for file access.
4 Command explanation: Check whether the parameters are correct according to the received command and perform the corresponding operation.
5 System development basis and chip selection (1) Selection and use of radio base station chip The base station chip is used for information communication between the contactless RF card and the central processing unit. The following chips can be used to read and write the CPU card conforming to the ISO14443 TYPA standard such as FM1208. Refer to related documents. This design is mainly based on cards, so for the specific application of the base station chip, you can refer to the relevant documents.
â—† Philips series chips: RC500, RC522, RC531, RC632.
â—†Fudan series chips: FM1702N, FM1702SL, FM1715N, FM1725N.
â—† TI's base station chips: RI-R6C-001A, TRF7960.
â—† EM company base station chip: EM4094, EM4294.
(2) Selection and use of single-chip microcomputer For the information processing of non-contact RF card, different schemes can be selected according to the requirements of function and speed. Various CPU chips have their own advantages and disadvantages.
â—† 8051 MCU: low price, simple entry, sufficient supply.
â—† AVR MCU: The price is moderate, the speed is fast, and the peripherals are rich.
â—†ARM: Powerful, fast, and can run RTOS.
(3) ISO14443-3, ISO14443-4
These two parts are the core of learning and operating a contactless CPU card.
1 ISO/IEC 14443-3 specifies the round robin of adjacent cards (PICCs) when entering adjacent coupling devices (PCDs), the character format, frame structure, and timing information of the communication initialization phase. REQ and ATQ command content, select one of the multiple cards, and other necessary parameters in the initialization phase. This part of the rule applies to both Type A PICCs and Type B PICCs.
2 ISO/IEC 14443-4 specifies the transport protocol for contactless half-duplex blocks and defines the steps for activating and stopping the protocol. This part of the transfer protocol applies to both Type A and Type B cards.
(4) IS07816-4
This part is the basis for learning and operation, SAM, which specifies: the content of messages, commands and responses sent by the interface device to the card and in the opposite direction; the structure and content of the history bytes sent by the card during the reset response The structure of the files and data seen at the interface when processing inter-industry commands for exchange; the method of accessing files and data within the card; the security architecture that defines the rights to access files and data within the card; secure message exchange Method; the method of accessing the algorithm handled by the card (these standards do not describe these algorithms).
6 SAM card application in the system According to the application method, the application of SAM card in the system can be divided into:
1 Hard key, that is, the SAM card holder is installed in the terminal tool, and all the authentication is performed by the SAM card installed in the SAM card holder. In this way, when the terminal tool is repaired, the terminal device is empty as long as the SAM card in the SAM card holder is taken out. Therefore, all banking equipment adopts the authentication mode of the SAM card.
2 soft key, that is, there is no SAM card holder in the terminal equipment. The operation of this key is actually completed by the terminal equipment, so that the customer's key is equal to the existence of the terminal equipment. When the manufacturer takes back the terminal equipment maintenance, it is extremely easy. Causes key loss.
Conclusion The cracking of the Mifare algorithm has sounded the alarm for the safety of the city utility IC card system. In the current era of rapid development of science and technology and information technology, only by continuously innovating and continuously improving the safety factor and technical level of the IC card system of urban public utilities can we achieve higher and further development and contribute to the development of information in the country. . The non-contact CPU card smart card technology is becoming a technologically up-and-coming option, and the era of replacing logical encryption cards with CPU cards has arrived.
Light Stand,Ring Light Stand,Photo Studio Light Stand,Mobile Phone Tripod Stand
SHAOXING COLORBEE PLASTIC CO.,LTD , https://www.colorbeephoto.com
